A few weeks ago news broke that Manwin’s sites have been compromised and tens of thousands of customers information may have been compromised. This hack included the Brazzers’s forums. Anyone who had an account there had their information compromised. While they were busy backtracking claiming the hack was no big deal they apparently forgot to sure up the security on their other assets because on February 23rd YouPorn got hacked [source] which compromised an estimated 1 million accounts and the hackers even posted the list of YouPorn users and their email addresses.
This is a big deal for a few reasons …
- First and foremost it directly links you to a site that illegal streams stolen porn which means that could potentially be used against you in those “John Doe Lawsuits” which could cost you hundreds or even a few thousands of dollars, depending on how active int he youporn site you were.
- Next it’s a big deal because the hackers posted every users email address and that means every jack ass spammer out there has taken that list and put it in their database. Now you are going to start getting way more spam.
- Now people know you are into porn. If you have enemies and are in a situation that viewing porn online could compromise you, well … an enemy could use that list against you.
- And last but surely not least, it’s a big deal because more often than not people use the same email address and password for multiple sites so if they stole them for one site, they may now have access to your other accounts like paypal and amazon and whatnot. So BE SURE AND CHANGE ALL YOUR PASSWORDS IMMEDIATELY!
So now it seems the hackers have struck another Manwin owned site again. Manwin (aka Brazzers) recently took control of Digital Playground including their family of websites and what they apparently forgot to do is make sure security was strong, especially after the their other sites started to get hacked.
So tonight Jesse Jane tweeted about her site being down, it’s been down over an hour now and her site isn’t alone. The main Digital Playground site is down as well.
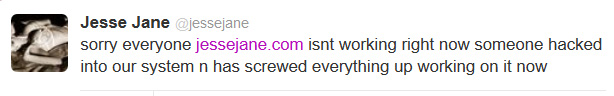 There is no official news who has hacked the site yet or what information (if any) will be exposed for the Digital Playground customers but since their DVD store was also hacked, it could potentially be a very big deal, including the loss of username and passwords as well as email addresses and credit card numbers and maybe (possibly) your home address!
There is no official news who has hacked the site yet or what information (if any) will be exposed for the Digital Playground customers but since their DVD store was also hacked, it could potentially be a very big deal, including the loss of username and passwords as well as email addresses and credit card numbers and maybe (possibly) your home address!


Poor Jesse. 🙁 I just checked and it seems her site is still down!
http://www.databreaches.net/?p=23518
The Digital Playground porn site has reportedly been hacked. Big time. The site that advertises “Porn worth paying for” may find itself paying dearly for a security breach that may have exposed over 72,000 customers’ details and over 44,000 credit card numbers.
In what they claim as their first release, a group calling themselves The Consortium (@Th3Consortium on Twitter) described the hack:
You see for a while now we have had access to digitalplayground.com, one of the five biggest porn sites in the world.
But it doesn’t need any introduction from us.
This company has security, that if we didn’t know it was a real business, we would have thought to be a joke – a joke that we found much more amusing than they will.
“This site has so many freaking holes that if I didn’t know it was a porn site, I would have mistaken it for a honeypot” – [Redacted]
We did not set out to destroy them but they made it too enticing to resist. So now our humble crew leave lulz and mayhem in our path.
We not only have the 72k users of this site but also over 40k plaintext credit cards including ccvs, names and expiry dates.
If you want to hear more about those plaintext credit cards scroll through the MySql info further down. And of course as this is a porn site
there was no shortage of .mil and .gov emails in their user list.
We also went on and rooted four of their servers, as well as gaining access to their mail boxes. Using credentials from emails
we tapped into their conference call. “Is anyone besides David on the line ?” – We were. Did we win? Sure looks that way.
Digital Playground game over.
Thankfully for the 72,794 users whose usernames, e-mail addresses and plaintext passwords were reportedly acquired, the hackers did not dump all of the data they claim to have acquired, but if they are possession of the data, that alone is cause for concern. They posted a smattering of the personally identifiable information they acquired:
27 admins’ names, usernames, e-mail addresses, and encrypted passwords
28 admins’ names, usernames, e-mail addresses, and encrypted passwords (some overlap with previous table)
85 affiliates’ usernames, plaintext passwords, and in some cases, IP addresses
100 users’ e-mail addresses, usernames (same as e-mail addresses) and plaintext passwords, and
82 .gov and .mil e-mail addresses with corresponding plaintext passwords
They did not dump the 44,663 credit card numbers that they claim to have acquired, but note that card numbers, card expiration date, cvv and all customer billing address and contact info were in plain text. They provided two redacted versions of named customers as proof of that.
Clearly, if their claims are true (and I have no reason to disbelieve based on what they posted), this is bad. Really bad. So much personal information stored in clear text? Seriously? From Digital Playground’s Privacy Policy:
1. Information Security
Digital Playground, Inc. is dedicated to the protection of Site users’ information. To prevent unauthorized access to information provided to us, the Company uses a number of generally accepted industry standard procedures designed to effectively safeguard the confidentiality of your personal information. These procedures include secure server location, controlled access to data and equipment, robust redundant firewall software, network monitoring, adaptive analysis of network traffic to track and prevent attempted network intrusions and other network abuse and appropriate employee training in the area of data security. We shall continue to take reasonable steps to provide effective data protection at all times, however, because no security technology can provide invulnerability to information compromise, the Company cannot, and does not, guarantee the security of any information that you transmit to us or to any third party affiliated with the Site.
Apparently their dedication doesn’t extend to encrypting customer data or PCI DSS compliance.
At the time of this posting, DP’s homepage returns an error message. They have not yet responded to an inquiry I sent them this morning about the claimed hack.
h/t, Dump Centa
Update: The web site is back up with no notice and I’ve received no response to my inquiry yet. Interestingly, Digital Playground is operated by Manwin – the same firm that operates the Brazzers and YouPorn web sites that were recently in the news when they were hacked. According to Manwin’s statement in the previous reports, this site appears to have had less security than Brazzers, as in that case, user passwords were reportedly encrypted and credit card data were not compromised.
Looked through some of the data dumb today. They had a lot of contract stars with passwords like “changeme” and those with admin powers would email each other sensitive information.
All credit card information was stored in plain text, easily viewable by anyone who directly accessed their database and they didn’t take steps to sure up the security on their database such as blocking out remote log ins.